
The Toyota Hilux Gen3 Denso ECU (AN120/AN130) (e.g. microcontrollers R7F701202/702) introduced new hardware and software compared to earlier models. In practice, Gen3 diesel Hilux Denso ECU often use a 0–5 V MAP sensor scaled to roughly 0–360 kPa (3.6 bar), whereas Gen2 Denso ECUs were limited to ~250 kPa. This requires re-scaling tables in the firmware. Our team at ReverseEngineer.net tackles these challenges with specialized tools and deep microcontroller expertise. In this article we explain our approach to Gen3 firmware extraction, finding the MAP calibration tables, and safely modifying them.
Gen2 vs. Gen3 Denso ECU Challenges
The Gen3 Denso ECU uses a Renesas RH850-series MCU, unlike the Gen2’s older architecture. It has more flash memory and often more advanced security (checksum and access-control schemes). The Gen3 firmware uses updated diagnostics protocols, so traditional OBD flashing tools may not work or are only recently supported. In many cases we must rely on bench access: removing the ECU and tapping directly into its circuit. On the board we locate hidden debug interfaces (e.g. JTAG/BDM) exposed on unpopulated pads. These are the gateways to low-level firmware access. Compared to Gen2, Gen3’s memory layout and code structure differ, but the principle remains: once we can dump the flash image, we can search it for the MAP sensor logic and tables.
Firmware Extraction and Flash Reading
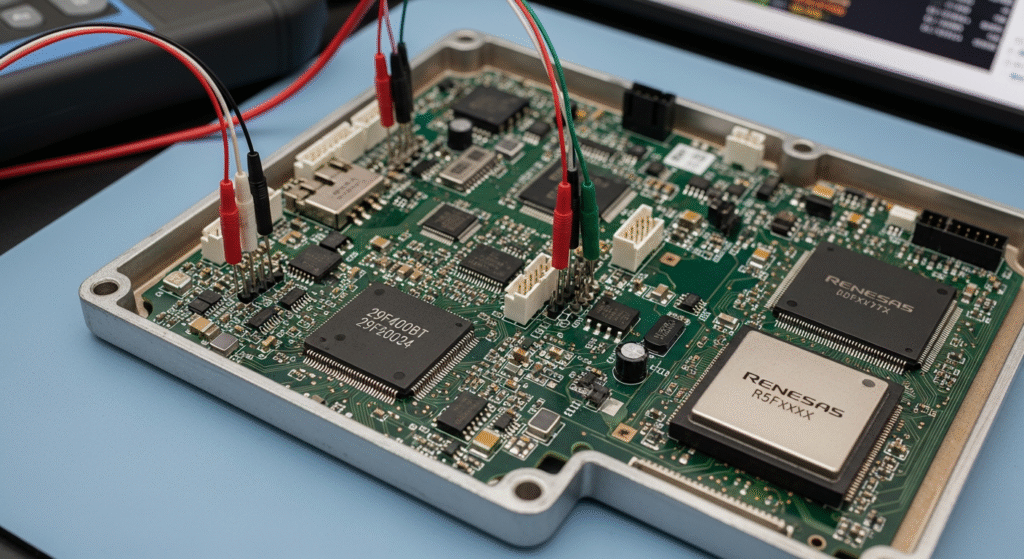
To extract the Gen3 Denso ECU firmware, we connect a custom bench programmer to the unit’s PCB. This often involves soldering wires or using spring-loaded clips on test points. As shown above, our bench flasher harness ties into the ECU’s power/ground and debug pins. In practice, we scan for empty connectors or solder pads that expose interfaces like JTAG. Once a debug link is established, our programmer reads the entire flash memory in a few minutes. We verify the dump by checking known header values and checksums.
If the ECU has software lockouts, we use hardware exploits. For example, security research shows that after bypassing the ECU’s authentication, one can execute code on the unit and gain full read/write memory access. We apply this by loading a small custom routine into RAM that sends back the flash contents. This yields a bit-for-bit firmware image. Throughout, our engineers maintain hash logs and chain-of-custody records to ensure integrity.
Locating MAP Sensor Calibration
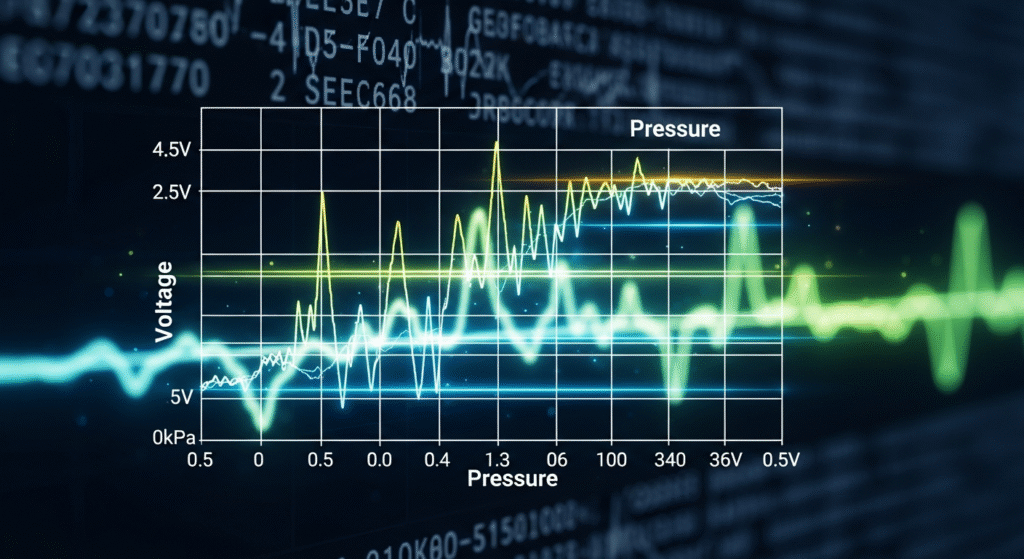
With the firmware image in hand, we search for the MAP sensor calibration data. Calibration tables are typically stored as contiguous numeric matrices with predictable patterns. We look for blocks of data with regular step sizes and monotonic progression for example, raw sensor voltages vs. pressure values. These data regions stand out because they have low entropy and structured spacing compared to code or strings. In practice, our engineers use automated entropy scans and pattern detectors (sliding-window variance, monotonicity checks, etc.) to highlight candidate regions. For instance, a 3-bar MAP scale might appear as a table where 0.5 V maps to 0 kPa and 4.5 V maps to ~360 kPa across an axis. We identify these by the table’s numeric progression and by correlating with known sensor behavior.
Once candidate tables are found, we perform axis inference. We capture synchronized engine telemetry (e.g. logged MAP voltage vs. actual boost pressure) and compute correlations with the table values. A high Pearson correlation confirms which table column is MAP voltage and which is pressure. This empirical axis-matching step ensures we have the correct MAP linearization. In short, we pattern-match using domain knowledge: contiguous low-variance data blocks are checked against expected MAP ranges, and then validated with real or simulated input.
ECU Firmware Reverse Engineering Techniques
Our engineers then use interactive disassembly tools to trace how the MAP table is accessed in code. In the analysis GUI (shown above), we align memory dumps with decompiled code to see where sensor values index the table. We search for the sensor’s ADC register or operand and follow code references to find the lookup operation. Often this involves identifying related constants or function calls around the table. We use industry-standard tools along with proprietary scripts to speed up this process. By recognizing known map layouts and interpolation routines, we pinpoint exactly where the MAP scaling lives in firmware.
Once located, we apply modifications carefully. For example, to change from a 360 kPa max to a 500 kPa MAP sensor, we would adjust the table endpoints and interpolation factors accordingly. Each change is verified in our bench simulator: we sweep the MAP voltage input and check that the ECU’s pressure reading response matches our intended scale, without causing faults.
ReverseEngineer.net Expertise and Services
Our team brings deep ECU reverse engineering experience to every project. We have tackled Denso ECUs, Bosch, Siemens and other ECUs across many platforms. For Toyota Hilux Gen3, we leverage in-house hardware flashers, custom analysis libraries, and decades of calibration knowledge. We conduct every step from removal, extraction, to coding under strict controls, with full documentation. We maintain proprietary catalogs of known ECU structures and use statistical algorithms to automate map discovery, backed by rigorous bench validation.
With these capabilities, ReverseEngineer.net stands as a technical leader in ECU firmware analysis. Our engineers are experts in RH850-class microcontrollers and ECU memory architectures. We follow best-practice workflows (hypothesis-driven map hunting, chained hashes, rollback images) to ensure reliable results.
Ready to Optimize Your Denso ECU? Our certified team can precisely scale your Gen3 ECU’s MAP sensor and all related calibrations. As noted on our site, “ReverseEngineer.net can help. Our expert engineers handle calibration extraction, map extraction, and comprehensive ECU reverse engineering”. Contact us today to schedule a consultation. We’ll deliver a hashed original image, identified calibration tables, and a detailed plan to adapt your ECU firmware, all with forensic-level traceability.
Let's Work Together
Need Professional Assistance with Reverse Engineering or Cybersecurity Solutions? Our Team is Ready To Help You Tackle Complex Technical Challenges.