
We recently received an inquiry from a client facing a legal dispute. Their concern?
“Can a person manipulate the dates of sent or received messages using WhatsApp Message Timestamp Manipulation and then transfer it back to the mobile phone?”
To support their appeal in court, our client required a forensic proof of concept to demonstrate that WhatsApp message timestamps can be manipulated and restored on a mobile device.
Following our preliminary discussions, we agreed on the scope, pricing, and timeline. The forensic investigation began the same day.
📌 This article has been written with the approval of our client. Sensitive details have been redacted for privacy and security reasons.
WhatsApp message timestamp manipulation is a real concern in digital forensics. Can WhatsApp message dates be altered? Can manipulated messages be used as legal evidence?
In this case study, we examine how WhatsApp Message Timestamp Manipulation can be altered at the database level and how our digital forensic experts detect such tampering.
The Rising Concern Over WhatsApp Message Timestamp Manipulation

In an era where digital evidence plays a major role in legal cases, the integrity of WhatsApp messages is being questioned more than ever. What if the timestamp of a message could be changed? Could manipulated messages be presented as real evidence in court?
This case study examines a real-life scenario where a client suspected that their WhatsApp chat history had been tampered with / the other party had changed the message dates and presented them as evidence in court. Using advanced digital forensics, we analyzed the feasibility of changing WhatsApp message timestamps and successfully demonstrated that message dates can indeed be changed at the database level.
Our Certified Digital Forensic Evidence Experts then wrote appropriate reports, signed the reports and made them suitable for presentation as evidence in court.
Understanding WhatsApp’s Backup System
WhatsApp employs a structured backup system to store chat histories, media, and other essential data. These backups play a critical role in message retrieval, forensic investigations, and potential manipulations.
There are two primary types of backups in WhatsApp:
Local Backups (Stored on the Device)
WhatsApp creates daily automatic backups on an Android device’s local storage.
📌 Storage Path:
/sdcard/Android/media/com.whatsapp/WhatsApp/Databases/
The latest backup is named msgstore.db
Older backups follow this format: msgstore-YYYY-MM-DD.1.db.crypt14
✔️ Key Forensic Considerations:
- Stored as SQLite database files (
msgstore.db) containing complete chat histories. - May or may not be encrypted, depending on the user’s end-to-end encryption settings.
- Extractable from a rooted device for forensic analysis.
2️⃣ Cloud Backups (Google Drive & iCloud)
WhatsApp allows cloud backups, but they are fully encrypted:
- Google Drive (Android users)
- iCloud (iOS users)
✔️ Key Security Factors:
- Cloud backups are always encrypted and require WhatsApp’s private key to decrypt.
- Timestamp modifications in cloud backups are NOT possible, as they can only be restored by WhatsApp.
- Only local unencrypted backups can be manipulated for forensic analysis.
How WhatsApp Stores Message Timestamps in the Database
The primary database file, msgstore.db, contains every message with a corresponding timestamp stored in Unix epoch format (milliseconds since January 1, 1970).
📌 Key Timestamp Fields in the Database:
timestamp→ The time the message was sent.received_timestamp→ When the recipient received the message.receipt_server_timestamp→ When WhatsApp’s server processed the message.
Example of raw timestamps stored in the database:
timestamp: 1741784749000 → (Converted to) → 2025-03-12 16:05:49
By modifying these timestamps, messages can appear as if they were sent months or years earlier or later than their actual transmission time.
Step-by-Step Digital Forensic Analysis for WhatsApp Message Timestamp Manipulation
Extracting the WhatsApp Database
For forensic investigation, we first extracted the msgstore.db file from the client’s device using root access.
📌 Database Location on Android:
/data/data/com.whatsapp/databases/msgstore.db
Analyzing the Message Timestamps
Using DB Browser for SQLite, we examined the message table and identified timestamps stored in the key fields mentioned earlier.
Modifying Message Timestamps
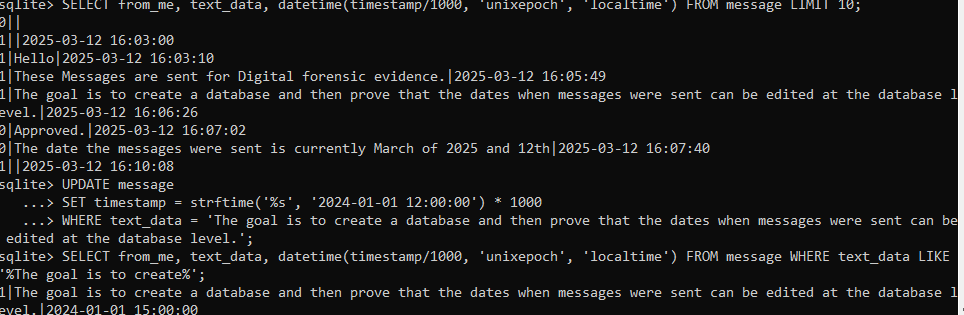
To alter timestamps, we executed the following SQL query to modify all message dates beyond 2022 to a date in 2024:
[code language="sql"]
UPDATE message
SET timestamp = strftime('%s', '2024-01-01 12:00:00') * 1000
WHERE timestamp > strftime('%s', '2024-01-01 00:00:00') * 1000;
[/code]
After applying similar modifications to received_timestamp and receipt_server_timestamp, we successfully altered the dates.
Re-Importing the Database and Testing
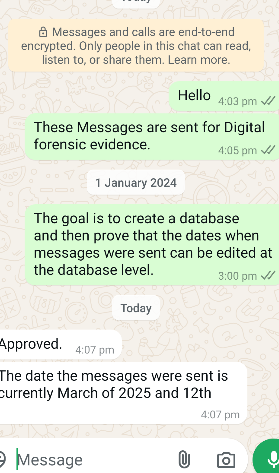
Once the modifications were complete, we replaced the original msgstore.db file on the client’s device.
Upon reopening WhatsApp, the manipulated timestamps appeared as if the messages were originally sent in 2024 instead of 2025.
Can WhatsApp Message Manipulation Be Detected?
Yes! Digital forensic analysis can detect WhatsApp message timestamp manipulation.
- By comparing local timestamps with server logs
- By analyzing delivery receipts & metadata inconsistencies
- By reconstructing backup files to identify tampering
For legal professionals, this proves that WhatsApp messages alone should NOT be treated as unquestionable evidence without forensic validation.
The Importance of Digital Forensics
This case study proves that WhatsApp message timestamps can be altered if an attacker gains access to an unencrypted backup. However, forensic experts can detect these changes through specialized investigation methods.
If you suspect that WhatsApp messages have been manipulated in a legal case, forensic validation is essential.
Need professional digital forensic analysis? Contact us today for expert investigation services!
Let's Work Together
Need Professional Assistance with Reverse Engineering or Cybersecurity Solutions? Our Team is Ready To Help You Tackle Complex Technical Challenges.