Reverse Engineering Toyota Hilux Gen3 Denso ECU for MAP Sensor Scaling
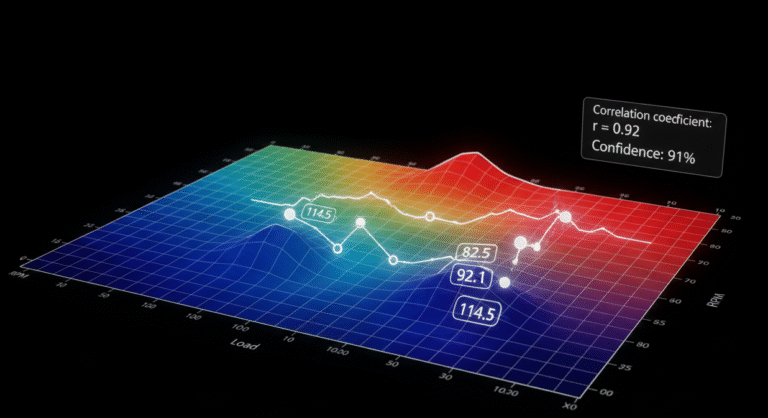
The Toyota Hilux Gen3 Denso ECU (AN120/AN130) (e.g. microcontrollers R7F701202/702) introduced new hardware and software compared to earlier models. In practice, Gen3 diesel Hilux Denso ECU often use a 0–5 V MAP sensor scaled to roughly 0–360 kPa (3.6 bar), whereas Gen2 Denso ECUs were limited to ~250 kPa. This requires re-scaling tables in the firmware. Our team at […]