What is Reverse Engineering?
Reverse engineering is the process of dissecting, analyzing, and understanding an existing system, software, or hardware without access to its original documentation or source code. The goal of this process is to gain insights into how the system works, allowing engineers, developers, and security researchers to modify, enhance, or recreate its functionality.
At its core, reverse engineering is like taking apart a puzzle and figuring out how each piece contributes to the bigger picture. It is widely applied in various industries, including:
- Cybersecurity: To analyze and neutralize malware threats.
- Software Development: To improve or recreate legacy applications.
- Hardware Analysis: To study and optimize physical devices.
- Digital Forensics: To uncover security vulnerabilities and reconstruct lost data.
Reverse engineering can be used for both ethical and unethical purposes, depending on the intent of the researcher. While it plays a crucial role in security analysis, software compatibility, and innovation, it is also used by hackers for unauthorized software modifications and piracy.
Reverse Engineering Definition
Technically, reverse engineering is the systematic process of deconstructing an object, program, or system to understand its internal mechanisms. This method is particularly valuable when working with proprietary software, encrypted binaries, or obfuscated code, where the original source is unavailable or deliberately protected.
The key objectives of reverse engineering include:
- Understanding Functionality: Identifying how a system or program operates internally.
- Recovering Lost Information: Reconstructing source code or technical specifications.
- Enhancing Compatibility: Adapting software or hardware for interoperability.
- Security Research: Finding vulnerabilities and strengthening system defenses.
- Bypassing Protections: Removing restrictions such as DRM (Digital Rights Management) or software licensing mechanisms.
Reverse engineering requires specialized knowledge and tools, such as debuggers, disassemblers, decompilers, and network analyzers. It can be performed at various levels, from binary code analysis to physical circuit examination, depending on the type of system being studied.
In modern computing, reverse engineering is extensively used for malware analysis, exploit development, firmware analysis, and digital rights management (DRM) circumvention. However, legal and ethical considerations must always be taken into account before engaging in reverse engineering activities.
The History of Reverse Engineering
Reverse engineering has been around for centuries, with its origins tracing back to military technology. Engineers would study captured enemy equipment to understand their capabilities. In modern times, it has evolved significantly, especially in the fields of software security and intellectual property research.
- 1940s-1960s: Reverse engineering of mechanical and military hardware.
- 1980s: Early software reverse engineering efforts to study proprietary software and optimize performance.
- 2000s-Present: Reverse engineering has become a core part of cybersecurity, malware analysis, and software compatibility research.
How Reverse Engineering Works
Reverse engineering can involve multiple steps depending on the target being analyzed. Generally, the process consists of:
- Data Collection: Gathering all available information about the target system.
- Disassembly & Decompilation: Breaking down compiled software or hardware components.
- Dynamic & Static Analysis: Studying the execution behavior and structure of the target.
- Modification & Testing: Applying changes and testing different hypotheses.
Types of Reverse Engineering
- Software Reverse Engineering: Disassembling and analyzing software code to understand its functionality.
- Hardware Reverse Engineering: Studying physical components to identify design patterns and vulnerabilities.
- Cybersecurity Reverse Engineering: Examining malware, exploits, and security protocols to develop countermeasures.
- Network Reverse Engineering: Analyzing network traffic, protocols, and encryption mechanisms.
- Binary Analysis: Decompiling executable files to retrieve source-like information.
- Malware Analysis: Studying malicious software to develop antivirus solutions.
- Industrial Reverse Engineering: Analyzing mechanical and electronic components to improve design.
Advanced Techniques in Reverse Engineering
Modern reverse engineering employs various advanced techniques, including:
- Deobfuscation: Removing code obfuscation techniques used in software protection.
- Symbolic Execution: Analyzing programs by treating inputs as symbolic variables.
- Dynamic Binary Instrumentation: Monitoring a program’s execution in real-time.
- Side-Channel Analysis: Extracting information based on unintended data leaks like power consumption and timing.
Real-World Examples of Reverse Engineering
Reverse engineering has played a crucial role in various industries:
- Security Research: Security firms use reverse engineering to analyze malware and develop countermeasures.
- Software Compatibility: Companies analyze competitor products to improve compatibility (e.g., Wine for running Windows programs on Linux).
- Game Security: Anti-cheat software is developed through analyzing exploits in multiplayer games.
- Automotive Industry: Reverse engineering is used to study car engine software and optimize performance.
Reverse Engineering Tools (2025 Updated)
Reverse engineering requires a diverse set of tools depending on the target system. The following are the most widely used and recommended tools in 2025 across software, hardware, and network analysis:
1. IDA Pro
- Type: Disassembler & Debugger
- Description: One of the most powerful tools for binary analysis, decompilation, and debugging. Widely used for malware analysis, security research, and software cracking.
- Key Features:
- Converts machine code into human-readable assembly
- Supports interactive debugging
- Can analyze PE, ELF, and Mach-O binaries
- Plugins for deobfuscation and virtualization analysis
2. Ghidra
- Type: Open-source reverse engineering tool
- Description: Developed by the NSA, Ghidra is an alternative to IDA Pro, providing powerful decompilation, disassembly, and debugging.
- Key Features:
- Supports x86, x64, ARM, MIPS, and more
- Automatic function identification
- Collaborative analysis – works well for teams
- Built-in decompiler to reconstruct C-like code
3. Radare2
- Type: Reverse engineering framework
- Description: A lightweight and flexible toolset for binary analysis, patching, debugging, and malware research.
- Key Features:
- Command-line and GUI support
- Hexadecimal editor and binary patching tools
- Scriptable using Python and other languages
- Works with ARM, x86, MIPS, and other architectures
4. x64dbg
- Type: Debugger for Windows applications
- Description: An open-source x86/x64 debugger specifically designed for Windows binary analysis.
- Key Features:
- User-friendly GUI
- Supports debugging PE and DLL files
- Code injection and breakpoint support
- Plugin system for extended functionality
5. Wireshark
- Type: Network protocol analyzer
- Description: Used for network packet analysis, protocol reverse engineering, and security auditing.
- Key Features:
- Live traffic monitoring
- Packet inspection and filtering
- Decryption support for SSL, TLS, and other protocols
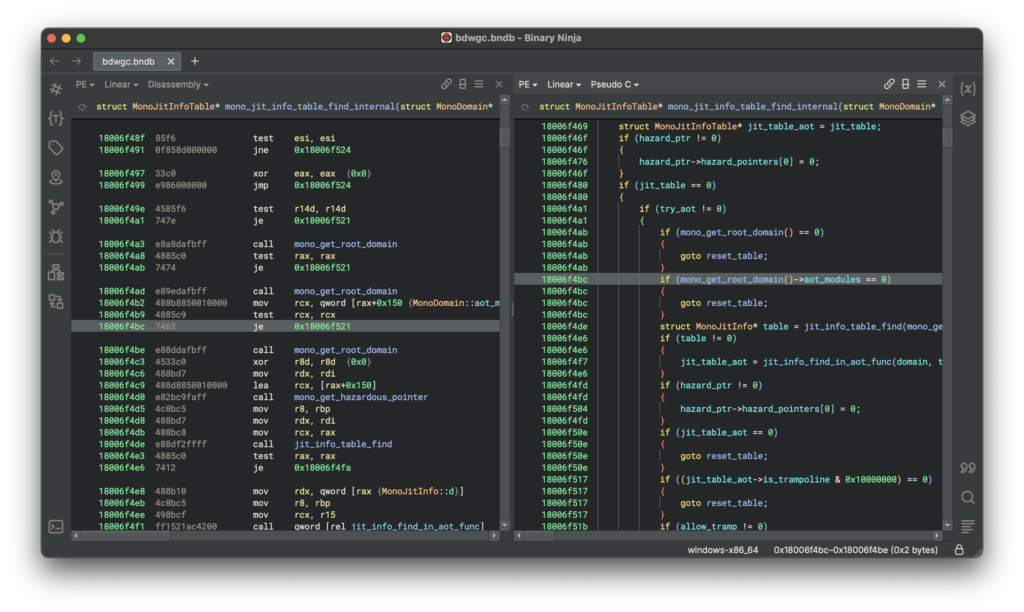
6. Binary Ninja
- Type: Interactive binary analysis tool
- Description: Known for automated decompilation, static analysis, and patching.
- Key Features:
- Intermediate language-based analysis
- Cross-platform compatibility (Windows, macOS, Linux)
- Plugin system for extending functionality
7. Frida
- Type: Dynamic instrumentation toolkit
- Description: Ideal for runtime analysis of applications, particularly mobile apps and IoT devices.
- Key Features:
- Injects scripts into running processes
- Works with Android, iOS, Windows, and macOS
- Can bypass anti-debugging mechanisms
8. Hopper Disassembler
- Type: macOS & Linux disassembler and decompiler
- Description: A powerful alternative to IDA Pro, specialized for macOS and Linux binary analysis.
- Key Features:
- Supports Objective-C and Swift analysis
- Decompiler for ARM, x86, and MIPS
- Integrated debugging capabilities
9. JEB Decompiler
- Type: Java and Android reverse engineering tool
- Description: Best for decompiling Android APKs and analyzing Java bytecode.
- Key Features:
- Extracts readable Java code from APK files
- Can modify and patch Android apps
- Handles obfuscated code well
10. Cutter (Radare2 GUI)
- Type: User-friendly GUI for Radare2
- Description: A great option for those who find Radare2’s command-line interface difficult.
- Key Features:
- Easy navigation of binaries
- Built-in decompiler support
- Plugin system for additional features
💡 Each tool has specific strengths. For beginners, Ghidra and IDA Pro are great starting points. For advanced users, Radare2 and Binary Ninja offer more customization and scripting capabilities.
Challenges in Reverse Engineering
While reverse engineering is a powerful tool, it faces significant obstacles, both technical and legal.
1. Code Obfuscation
Modern software often uses code obfuscation techniques to make reverse engineering difficult. These methods include:
- Control Flow Flattening: Making execution paths harder to analyze.
- Opaque Predicates: Inserting fake conditional branches.
- Dead Code Injection: Adding unnecessary operations to confuse decompilers.
- String Encryption: Hiding API calls and key functions.
🔴 Solution: Advanced static and dynamic analysis techniques, like symbolic execution and pattern recognition, help bypass obfuscation.
2. Anti-Debugging Mechanisms
Many applications include anti-debugging measures to detect and prevent reverse engineering. Common methods include:
- Debugger Detection: Checking if a debugger is attached.
- Timing Analysis: Delaying execution to prevent step-by-step debugging.
- Virtual Machine Detection: Preventing execution inside sandbox environments.
- Self-Modifying Code: Altering instructions during runtime to evade analysis.
🔴 Solution: Using stealth debugging techniques, such as API hooking and hardware breakpoints, can help circumvent these protections.
3. Strong Encryption and Cryptographic Protections
One of the biggest obstacles in reverse engineering is strong encryption used to protect sensitive data, software logic, and proprietary algorithms. Modern applications, particularly those handling DRM (Digital Rights Management), secure communications, and authentication mechanisms, often employ advanced cryptographic protections to make reverse engineering nearly impossible.

Common Encryption Techniques Used in Software Protection
🔐 Code Encryption & Packing
- Many software developers encrypt or pack their binaries using tools like VMProtect, Themida, and Code Virtualizer to make static analysis difficult.
- These tools dynamically decrypt parts of the code at runtime, preventing reverse engineers from obtaining a clean disassembly.
🔐 Asymmetric Cryptography (RSA, ECC, etc.)
- Software and hardware systems often use asymmetric encryption (public/private key pairs) to protect sensitive operations.
- Even if a reverse engineer extracts a public key, they cannot decrypt the data without the private key.
🔐 Symmetric Encryption (AES, ChaCha20, etc.)
- AES (Advanced Encryption Standard) and ChaCha20 are widely used to encrypt stored data, API keys, or communication protocols.
- Encrypted strings, configuration files, and communication packets require decryption keys, which may be hidden deep inside memory or hardware.
🔐 Obfuscated Key Storage & Dynamic Key Generation
- Some applications do not store decryption keys in static locations but generate them dynamically based on CPU instructions, execution time, or user behavior.
- This makes it challenging to extract the key using traditional reverse engineering techniques.
🔐 White-Box Cryptography
- A technique that hides encryption keys even when the software is being analyzed in memory.
- Used in DRM systems, mobile payment applications, and secure authentication modules.
- Even if an attacker extracts the entire algorithm, they cannot retrieve the actual encryption keys.
How Reverse Engineers Attempt to Bypass Strong Encryption
💡 Memory Dumping
- Attackers monitor program execution and extract decrypted data from RAM.
- Tools like Cheat Engine, x64dbg, and Frida allow runtime memory inspection.
💡 Hooking API Calls
- Reverse engineers can intercept API functions that handle encryption and decryption.
- Common targets include CryptDecryptMessage, BCryptDecrypt, and OpenSSL functions.
💡 Side-Channel Attacks
- Instead of breaking encryption, attackers analyze power consumption, execution time, or electromagnetic signals to infer the key.
- Common in hardware reverse engineering (smartcards, embedded devices, IoT).
💡 Brute-Force and Dictionary Attacks
- While impractical for strong cryptography, weak implementations (e.g., hardcoded passwords, poorly generated keys) can still be cracked using brute-force tools.
💡 Fault Injection and Hardware Attacks
- Used to manipulate encryption operations by introducing voltage glitches, laser pulses, or electromagnetic interference.
- Particularly useful in chip-level reverse engineering (e.g., attacking secure bootloaders, firmware encryption).
Strong encryption is one of the most powerful defenses against reverse engineering, making it nearly impossible to retrieve sensitive data or bypass protections without advanced attack techniques. While modern cryptographic protections are robust, flaws in implementation, key management, and software design can still provide entry points for reverse engineers.
✅ Understanding encryption techniques is crucial for both defending against cyber threats and developing better reverse engineering methodologies for security research, malware analysis, and penetration testing.
4. Binary Complexity and Virtualization
Some applications use virtualized code execution, such as VMProtect, Themida, and Code Virtualizer, making decompilation extremely difficult.
- Instruction Virtualization: Rewriting program code to run on a custom virtual CPU.
- Rolling Encryption: Constantly changing decryption keys at runtime.
- Packers & Protectors: Tools like UPX, Armadillo, and ASProtect obscure binary contents.
🔴 Solution: Dynamic analysis, memory dumping, and devirtualization techniques can help recover the original instructions.
5. Lack of Documentation & Complex Architectures
Reverse engineering can be challenging due to:
- No access to source code or documentation.
- Highly optimized assembly code that lacks readable structure.
- New CPU architectures requiring specialized analysis.
🔴 Solution: Community resources, prior research, and automated decompilers like IDA Pro or Ghidra assist in reconstructing complex binaries.
Reverse engineering is a powerful technique used in various fields, from cybersecurity to hardware analysis. Whether for security auditing, software development, or research, it provides valuable insights into how systems function. However, ethical considerations and legal boundaries should always be taken into account.
Let's Work Together
Need Professional Assistance with Reverse Engineering or Cybersecurity Solutions? Our Team is Ready To Help You Tackle Complex Technical Challenges.